Source: CNN
The latest figure comes from a report by the American Road and Transportation Builders Association, a group that advocates for strong investment in transportation infrastructure. Using data from the Federal Highway Administration, the group releases an annual Deficient Bridge Report.
This year’s report, looking at data from 2017, found:
- There are 612,677 bridges in the United States.
- Of them, 54,259 are “structurally deficient,” which means they have at least one key structural element in poor condition.
- That’s almost 9% of all US bridges, and the figure includes famous ones like the Arlington Memorial Bridge and the Brooklyn Bridge.
- Americans cross these structurally deficient bridges 174 million times each day.
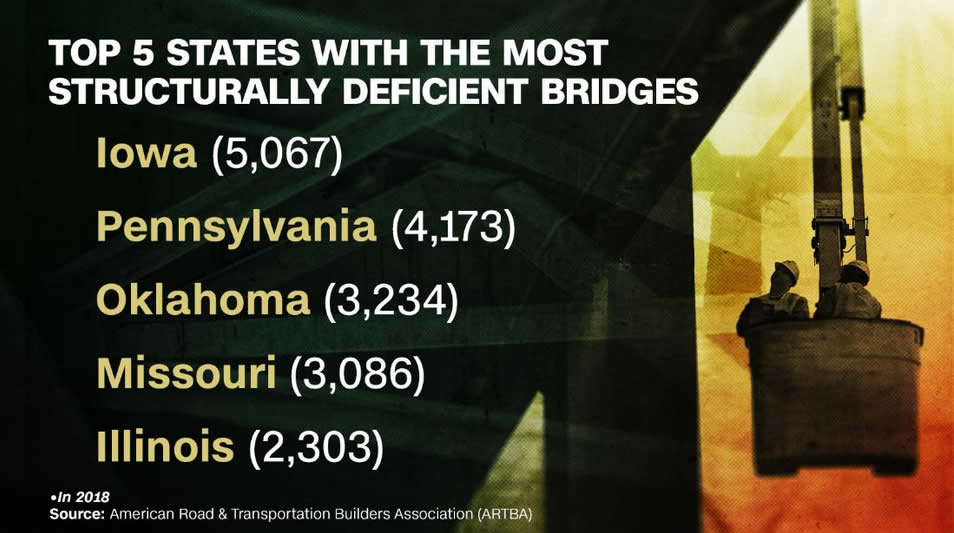
The report found that the largest number of defective bridges are in:
- Iowa
- Pennsylvania
- Oklahoma
- Missouri
States with the smallest number of structurally deficient bridges are: Hawaii Delaware Nevada
What it means to be structurally deficient
Bridges are regularly rated for safety on a scale of 0 to 9, with 9 meaning “excellent.” In order to be considered structurally deficient, one of its major components must measure 4 or below. Being structurally deficient does not necessarily mean that the bridge is unsafe, but it does mean it’s in need of repair. Repairing the deficiencies is critical. Deteriorating bridges can lead to road closures…